The new Azure Portal (https://portal.azure.com) has been up and running for quite some time. We’re finally seeing some Azure AD love in the new portal, albeit still in preview. This walkthrough is about how to assign Azure AD application permissions in the new portal.
This post assumes that you’ve already created your Azure AD Application. If not, check out an easy way to do that, here: https://www.jonathanhuss.com/automate-creation-azure-ad-application. This post will continue with the app that was created in that post.
Assigning Permissions
We’ll start by making our way to the Azure Active Directory Registered Applications blade (https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/RegisteredApps).
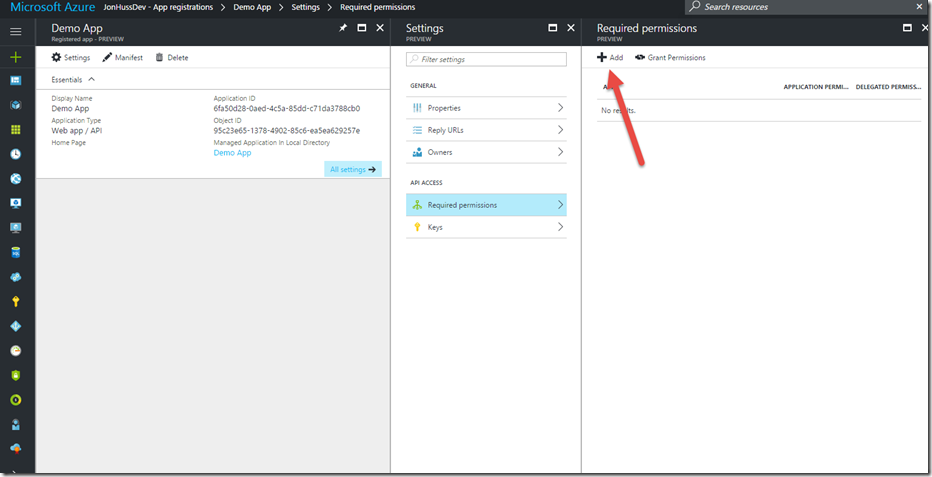
The new application should already be in the list. We’ll select it, which takes us to the Application Overview page. From there, the Required permissions link will allow us to add the various permissions for services.
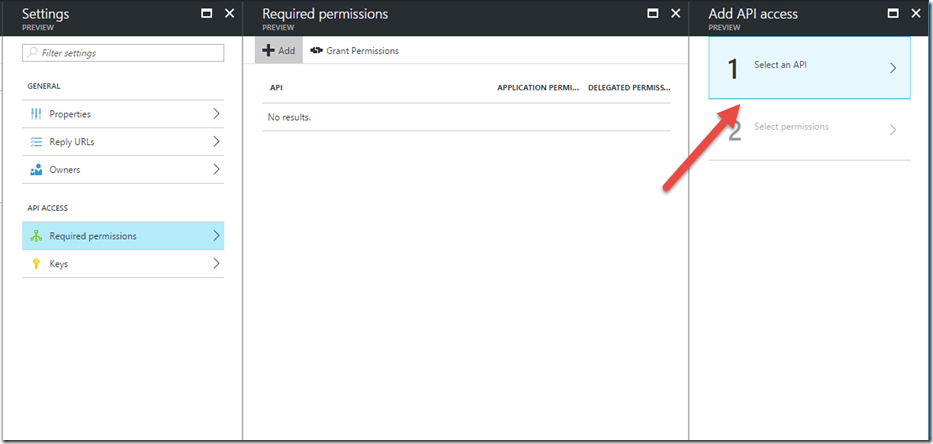
On the blade that opens from there, click the Add button:
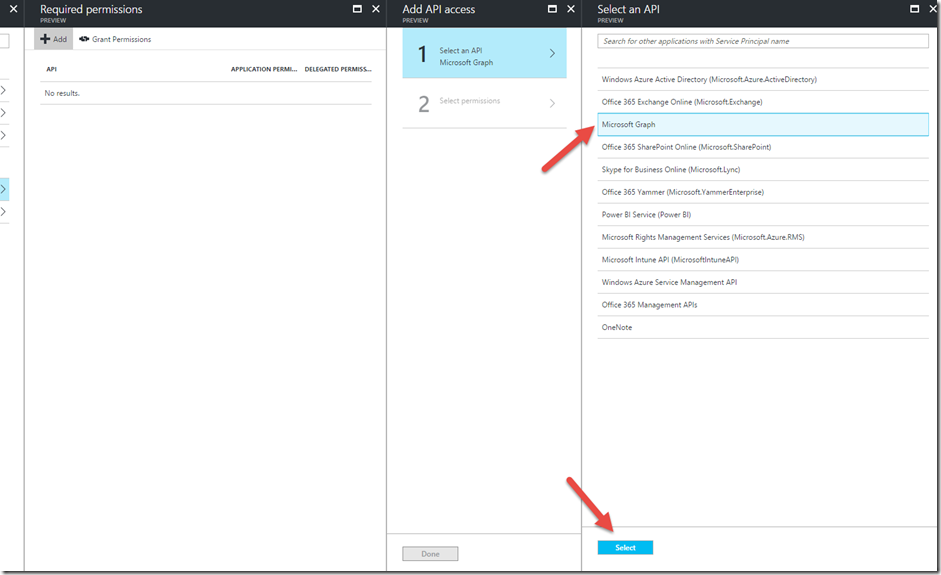
On the next blade, choose ‘Select an API’
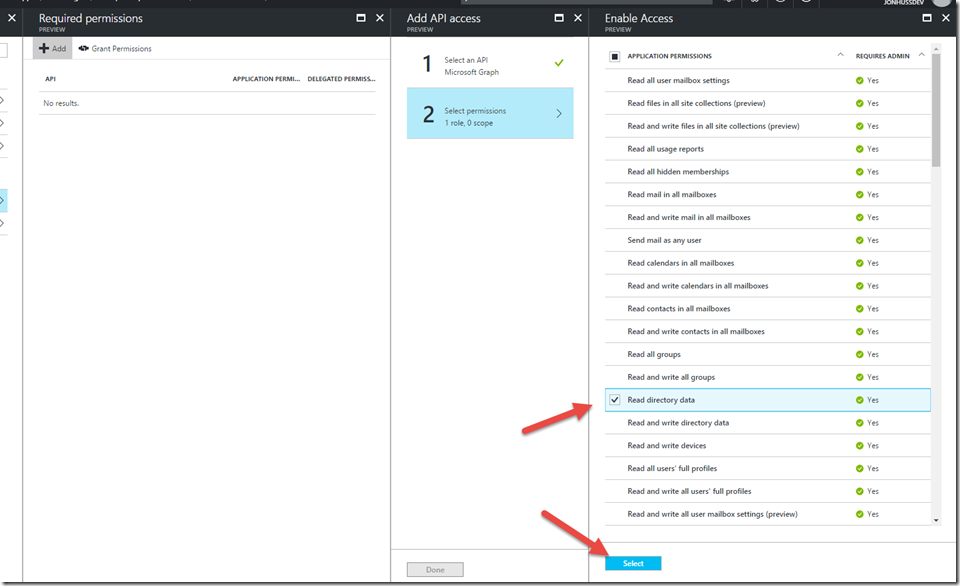
For the sake of this walkthrough, let’s setup permissions for Microsoft Graph. We’ll choose Microsoft Graph from the list and click Select
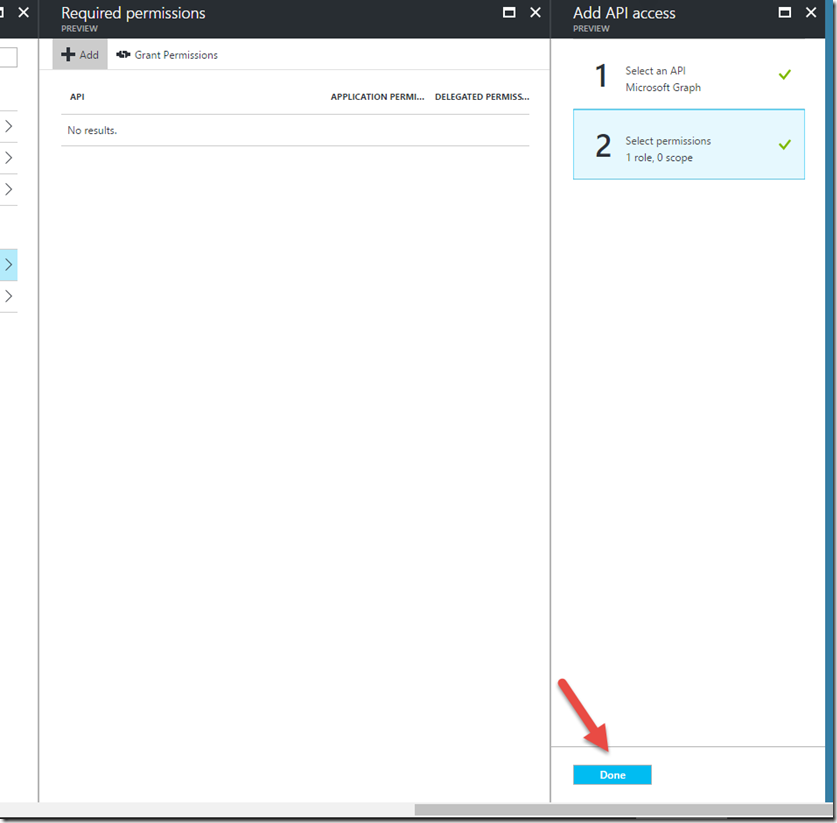
This will automatically take us to the Select permissions option. In that window, let’s choose Read directory data and click Select.
This will close the blade. We’ll click Done on the next blade:
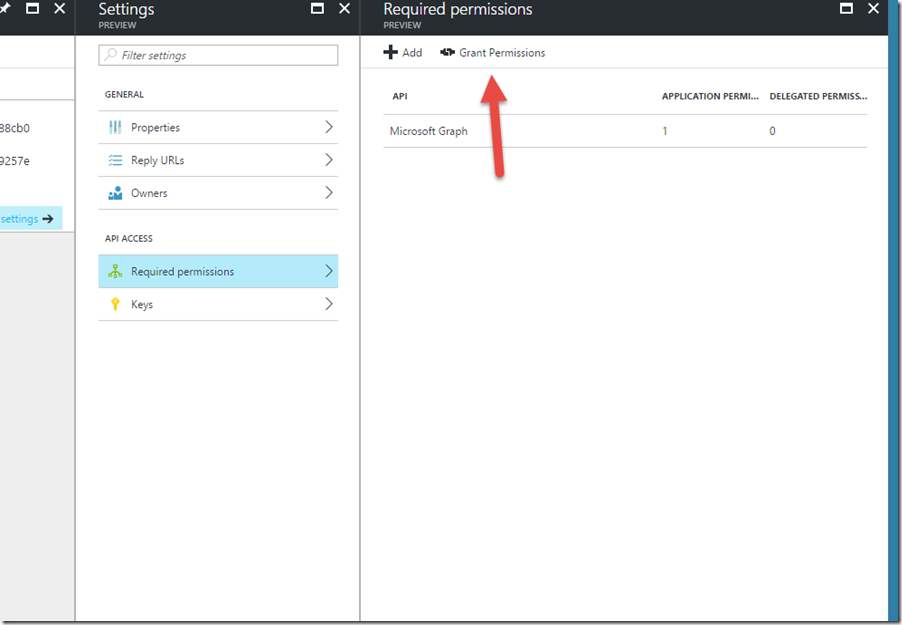
Finally, and this is important, we need to click ‘Grant Permissions’ to actually enable those permissions.
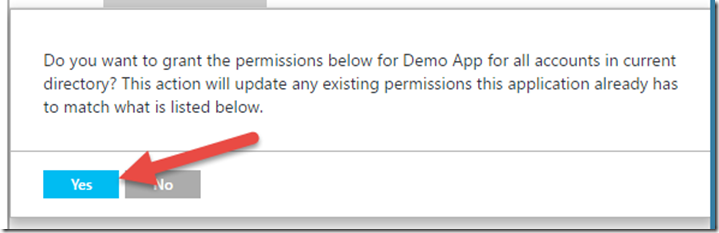
After clicking Grant Permissions, we should see a screen like the following. Click Yes
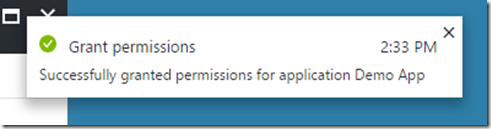
If all went well, we should see a notification that the permissions grating was successful for the app:
That’s it! Our application now has permissions to query the Microsoft Graph!
Notes
If you are not an admin with sufficient permissions of your own to grant permissions to the application, then you’ll need to find an admin who does have those permissions to consent to these permissions. Those of us who are tenant admins in our dev environments certainly have sufficient permissions to grant those permissions to ourselves.
If the permissions need to be changed, then we’ll need to go through the Grant Permissions process again. Same as before, an admin with sufficient permissions will need to consent to the application permissions.
Also, check out this GitHub repository: https://github.com/JonathanHuss/AzureADAppDemo. It has both the sample script and a demo .NET application.
![image_thumb[2] image_thumb[2]](https://www.jonathanhuss.com/wp-content/uploads/2017/03/image_thumb2_thumb.png)